Recommended BYOD and BYOM Security Setups and Best Practices
- BenQ
- 2023-08-28

There are several key differences between “bring your own device” (BYOD) and “bring your own meeting” (BYOM) and how the two approaches are applied at workplaces.
For BYOD, the Host Receiver coordinates screen casting from various devices that have direct reception from a transmitter (i.e., BYOD or Wireless Presentation System button). BYOD has user devices talking directly to the Host Receiver, which then delivers mirrored presentation data to a large display. The presentation data can be limited to only the people in the room, and you don’t even need to connect to the internet if you use a wireless presentation system (WPS) like the BenQ InstaShow WDC series
For BYOM, the Host Receiver doesn’t just passively receive data from a transmitter (TX), but also needs to allow BYOM devices such as laptops access, so those may collect all the data transmissions connected to the Host Receiver, including all-in-one video conferencing devices and the display.
That is to say, while in BYOD devices talk to a Host Receiver that mirrors them onto one big screen, in BYOM the Host Receiver allows devices to mirror or cast not just to a big screen, but requires more permissions for data security and control over who can access the Host Receiver, and thus creates more security risks.
In a hybrid meeting, through accessing the data in the Host Receiver, the BYOM laptop (i.e. Meeting Host) can synchronise the casting of the in-room meeting onto the local screen with remote participants. However, if any laptop can freely access the data in the Host Receiver, the control of confidential meeting data becomes challenging. To ensure effective control of sensitive information, a security mechanism can be implemented between the Host Receiver and laptops.
Therefore, to ensure data security in BYOM setups, controlling access becomes paramount. Implementing WPA2-Enterprise to regulate laptop access is crucial to prevent unauthorised entry into the Host Receiver.
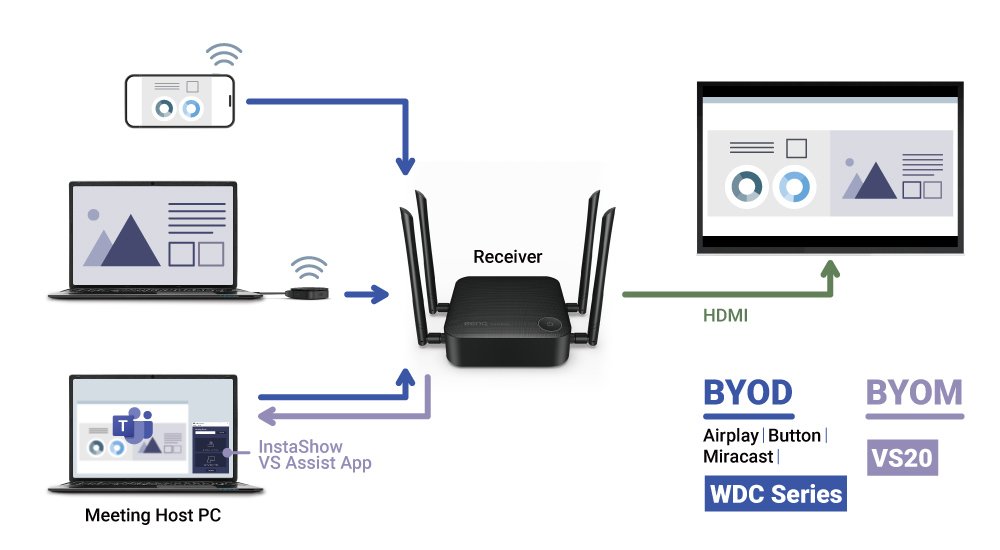
Comparing BYOD and BYOM topologies.
To ensure data security, there are three layers for BYOM protective set up recommendations:
An indirect connection is the first layer of security for BYOM. Companies aiming for optimal security and protection may opt for indirect connection.
In this setup, as the diagram shows, you establish an indirect connection where the Host Receiver and employee laptops are linked to the intranet rather than via a direct connection to the internet. The intranet can provide the firewall and the Active Directory (AD) server for security and protection against unauthorised snooping or intrusion.
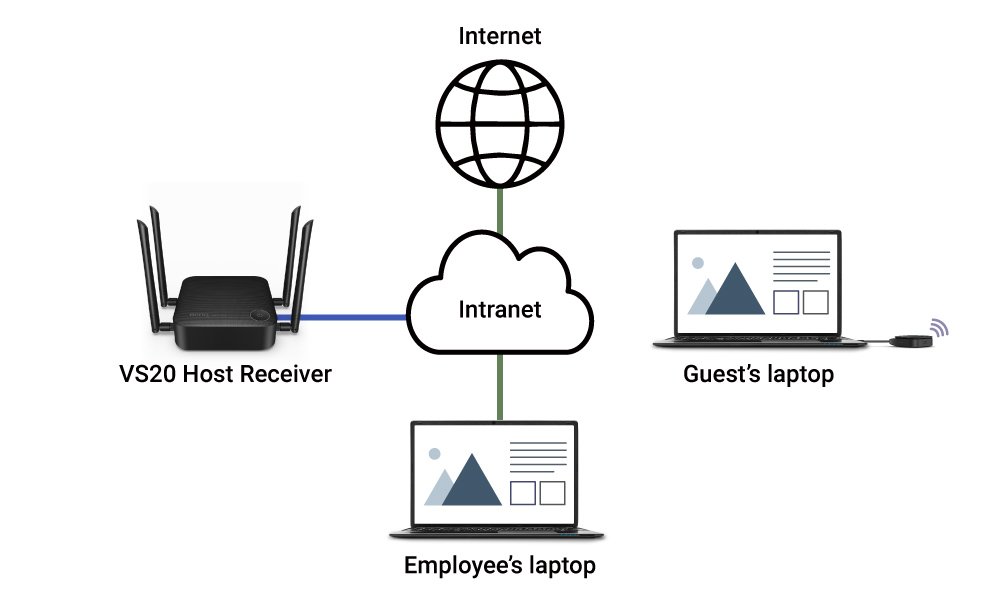
BYOM Indirect Connection to the InstaShow VS20 Host
The second protective BYOM layer is enabling WPA2-Enterprise with setup for guest SSIDs. With that, you can have a separate SSID for employees and a dedicated SSID for guests, with different access privileges to prevent unauthorised data accessing and sharing.
The third layer is the use of a pin code. BYOM users need to input a pin code in order to get access to the Host Receiver. The pin code is only given to people that are in the meeting room itself, so this way ensures presentation data remains limited to only the people in the room. If you have guests joining you locally, simply connect them with a WPS button so you don’t even need to connect to the internet to mirror to the big screen. InstaShow VS20 pin code functionality added Nov 2023.
For guest laptops, a simplified approach is recommended. Provide guests with a BYOD or WPS button for content casting, eliminating the need for network connectivity. Additionally, configuring a guest SSID adds an extra layer of protection.
For BYOD, users transmit one way to the Host Receiver, which then mirrors content to a large screen. But there’s no “crosstalk” among user devices, and users do not have access to the Host Receiver’s resources. Like with the BenQ InstaShow WDC series, which offers a dedicated BYOD, or WPS button that’s free from the internet so presentation data can be limited to only the people in the room. This ability offers sufficient security for BYOD situations.
For BYOM, communication is two-way, with at least the meeting host laptop being able to access the Host Receiver and other devices that take part in the meeting. Therefore, the three layers of security described above must be in place. We strongly recommend you implement the three layers we detailed, all of which are supported and enabled by InstaShow VS20 for the best possible organisational security, confidentiality, and peace of mind.
Want to learn more about how BenQ InstaShow VS20 makes secure BYOM possible?
Recommended Articles
-
Trends & Knowledge
BYOM and the Most Effective Wireless Conferencing Solutions
The BenQ InstaShow® VS20 system delivers enterprise-class video conferencing, screen sharing, and hosting for multiple BYOM participants, promoting successful hybrid work.
2023.05.12 -
Trends & Knowledge
How to Choose a Suitable Wireless Presentation System for Hybrid Meetings
A WPS suitable for the hybrid meeting era is one that is able to efficiently broadcast all the elements. But how to choose a suitable wireless presentation system for hybrid meetings…
2023.03.23 -
Trends & Knowledge
How to Start a Hybrid Meeting with BenQ InstaShow® VS20
BenQ InstaShow® VS20 integrates hassle-free video conferencing capabilities into Wireless Presentation System (WPS). This article shows how to use VS20 for hybrid meetings in three steps…
2023.04.27
